The Hidden Risks Lurking in App-to-App Connections
As SaaS ecosystems grow, app-to-app connections have become the backbone of modern productivity, enabling seamless workflows and enhancing efficiency. However, with these benefits come unprecedented security challenges. Many organizations remain unaware of the risks posed by interconnected apps—particularly when unmanaged or poorly configured connections expose sensitive data.
Shadow it, sprawling SaaS environments, and blind spots in identity management compound the problem. Even trusted apps with IT approval often carry hidden risks through excessive permissions, unmonitored API keys, or non-human identities that need proper oversight.
Recent Breaches Highlight the Danger
1. Microsoft Blizzard Breach (2024)
In this high-profile incident, attackers exploited app-to-app connections to escalate privileges within Microsoft’s ecosystem. By targeting non-human identities such as API keys, attackers bypassed traditional defenses, gaining access to sensitive data and moving laterally across interconnected apps. The breach underscored how poorly managed app permissions can leave even tech giants vulnerable.
2. MOVEit Transfer Exploit (2024)
In another notable breach, attackers leveraged vulnerabilities in app-to-app integrations to infiltrate systems using compromised credentials. This breach affected dozens of organizations, exposing sensitive customer data and creating a cascade of security failures. The lack of visibility into interconnected applications contributed to the delay in detection and response.
The Core Challenges of App-to-App Connections
1. Shadow IT and SaaS Sprawl
Unmanaged apps adopted without IT oversight create a fragmented security landscape. These “shadow IT” tools often fall outside the organization’s established SSO framework, relying on weak or reused credentials. Without integration into centralized identity management, these apps become blind spots, exposing the organization to risks that remain undetected until it’s too late.
2. Identity Visibility Gaps
With hundreds of apps and countless permissions, organizations struggle to track who has access to what. Non-human identities, such as API keys, further complicate visibility, leaving security teams blind to potential entry points for attackers. These blind spots make it nearly impossible to enforce policies like the principle of least privilege, where users and applications should only have the access required to perform their roles.
3. Excessive Permissions and Overlooked Risk Paths
Many apps are granted default permissions that exceed what’s necessary, creating unnecessary exposure. Attackers exploit these trust relationships between apps to move laterally within the network, escalating their privileges and gaining access to sensitive systems. Without intelligent permissions analysis, these risks go unnoticed, putting critical data at risk.
The Cost of Inaction
Failing to address app-to-app supply chain risks can lead to devastating consequences. The financial impact of a breach tied to app vulnerabilities is staggering. Recent reports show that the average cost of a data breach has risen to over $4 million, with app-to-app vulnerabilities accounting for a growing percentage of these incidents. For large organizations, these costs can escalate further, with downtime, legal fees, and lost revenue adding millions more to the bill.
Operational disruption is another significant consequence. Compromised app connections can cripple critical workflows, bringing business operations to a halt. Teams that rely on interconnected apps for collaboration, data sharing, or customer service may find themselves locked out or dealing with corrupted systems. These disruptions can tarnish customer relationships and erode trust in your organization’s ability to deliver.
Regulatory penalties present yet another risk. Non-compliance with data protection frameworks such as GDPR, HIPAA, or CCPA can result in hefty fines and increased scrutiny. In many cases, breaches caused by mismanaged app connections expose sensitive customer or employee data, violating these regulations and leading to costly legal repercussions.
The reputational damage of a breach cannot be overstated. Customers, partners, and stakeholders are less likely to trust an organization that cannot secure its digital ecosystem. A single breach can undo years of brand-building and customer loyalty, with long-lasting consequences for your bottom line.
Breaking the Illusion of Security
Many organizations believe their SSO solutions provide full protection for their SaaS ecosystem. While SSO is a powerful tool for centralizing authentication, its effectiveness is only as strong as its coverage. Shadow IT and unmanaged app connections often bypass SSO, creating blind spots that attackers can exploit. This false sense of security leaves organizations vulnerable to identity breaches, lateral movement, and data exposure.
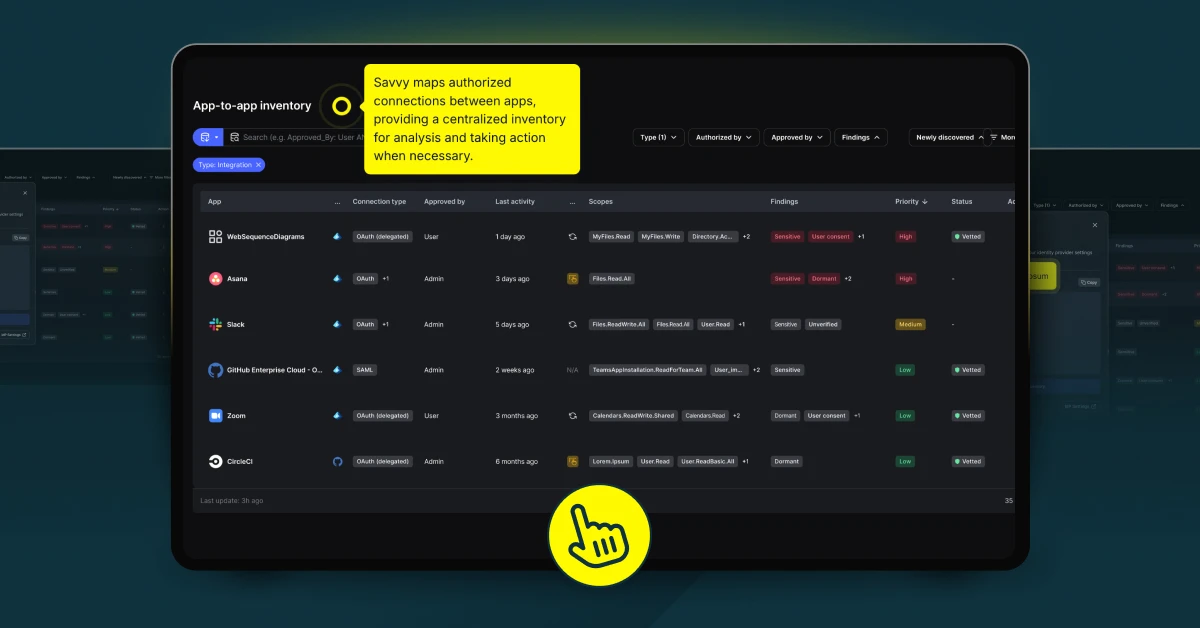
Savvy breaks this illusion by providing a complete view of your app-to-app connections. With Savvy, you gain the visibility, insights, and tools to close security gaps and protect your SaaS ecosystem.
Protecting the App-to-App Supply Chain
Savvy is purpose-built to address these challenges with an identity-first approach that delivers unmatched visibility, proactive risk management, and hands-free remediation.
Step 1: Comprehensive Identity and App Mapping
Savvy creates a detailed inventory of all human and non-human identities, app authorizations, and their associated permissions. By mapping every connection, Savvy uncovers hidden vulnerabilities, such as excessive permissions or dormant app connections.
Step 2: Risk-Based Prioritization
Savvy’s advanced analytics evaluate each app’s security posture, flagging high-risk connections for immediate attention. Whether it’s an app with sensitive scopes or a rarely used connection with broad permissions, Savvy ensures that security teams focus on critical vulnerabilities.
Step 3: Intelligent Permissions Analysis
Savvy goes beyond discovery by analyzing permissions and highlighting over-privileged access. This proactive approach reduces the risk of sensitive data exposure, even in technically “approved” apps.
Step 4: Real-Time Monitoring and Automated Remediation
Savvy continuously monitors app-to-app interactions, detecting anomalies and containing threats in real-time. Automated workflows ensure immediate remediation, eliminating the manual burden on IT teams while maintaining security at scale.
App-to-app connections are essential for modern businesses, but they also present unique security challenges. Without proper visibility and management, these connections can become a liability, exposing your organization to financial losses, operational disruptions, and reputational damage.
Savvy Security empowers organizations to understand, manage, and secure their app-to-app connections. By delivering unparalleled visibility, proactive risk management, and continuous monitoring, Savvy helps organizations stay ahead of evolving threats.
Are your app-to-app connections truly secure?