Identity takes center stage
In 2024, identity solidified itself as the de facto security perimeter for modern enterprises. Yet blind spots—like SSO Bypass, misconfigured MFA, and credential hygiene—remain major issues that most organizations miss entirely. To stay ahead of breaches, we predict organizations will begin to tackle these gaps in 2025 in order to fortify their Identity and Access Management (IAM) programs.
A string of high-profile SaaS breaches in 2024 underscored the urgency of addressing these blind spots. Russian attackers known as Midnight Blizzard exploited legacy OAuth misconfigurations to infiltrate Microsoft systems, accessing senior executives’ emails. Similarly, attackers breached Cloudflare’s Atlassian instance, using OAuth tokens to exfiltrate sensitive code repositories. Meanwhile, lax SSO and MFA enforcement and dormant accounts exposed Snowflake customers to credential-based attacks.
Unaddressed identity gaps drive increased breach activity
SSO bypass circumvents security controls
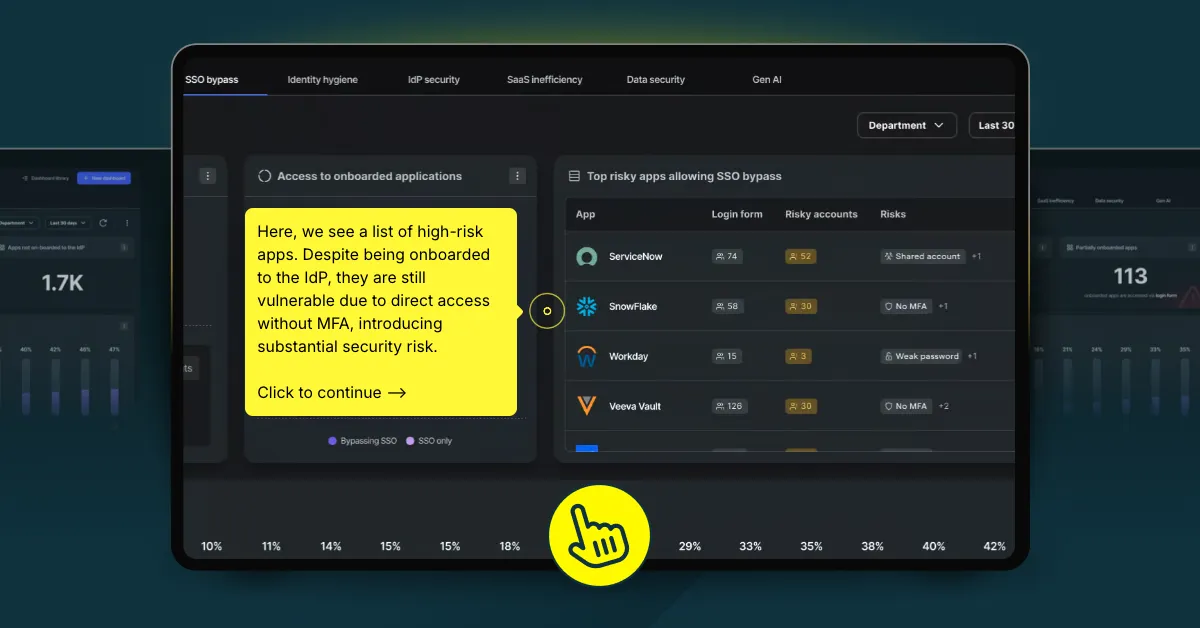
Users bypassing Single Sign-On (SSO) and logging in directly can expose critical vulnerabilities in an organization’s defenses. When SSO policies aren’t uniformly enforced, users may authenticate directly to applications using credentials outside centralized control, creating an entry point for attackers. This circumvention undermines SSO’s benefits and leaves sensitive systems unprotected. Without the visibility to detect and prevent these direct logins, organizations risk breaches that exploit these unmanaged access points.
Prediction: In 2025, expect breach incidents to rise as attackers leverage stolen credentials to bypass SSO and gain access to sensitive information through local accounts.
MFA issues lower the bar for unauthorized entry
Failing to implement multi-factor authentication (MFA) makes it significantly easier for attackers to breach accounts and systems. Without MFA, a compromised password—whether obtained through phishing, brute force, or leaked data—is often the only barrier between an attacker and sensitive information. Additionally, variations in how apps implement MFA can make it difficult to ensure that MFA remains actively enabled after initial configuration. Finally, when MFA is applied to centralized accounts while unprotected local accounts remain, organizations can have a false sense of security, further illustrating how SSO bypass can lead to breaches.
Prediction: Organizations lacking visibility and control over MFA enforcement will face increased security incidents related to credential-based attacks.
Poor credential hygiene practices expose an achilles heel
Weak, reused, shared, and compromised credentials weaken an organization’s identity security posture, undermining advanced security controls and enabling trivial cyberattacks. When credentials are predictable or reused across systems, attackers can exploit them through brute force, credential stuffing, or phishing attacks, gaining unauthorized access to sensitive information. Shared credentials amplify risks by reducing accountability and increasing exposure to insider threats or accidental breaches. Worse still, compromised credentials can circulate on the dark web, enabling bad actors to infiltrate systems unnoticed. This lack of credential hygiene not only jeopardizes data integrity but also erodes trust, fuels compliance failures, and incurs costly damages from downtime and remediation.
Prediction: Organizations without robust credential hygiene remediation tools and processes will experience a disproportionate share of breaches as compared to orgs with these programs in place.
Why Traditional Approaches Won’t Work in 2025
Organizations have made significant investments in tools like Identity Governance and Administration (IGA) and SaaS Security Posture Management (SSPM). While these tools provide essential support, they often operate exclusively on apps and accounts known to the IT and security teams. And even when accounts are known, the relationship between known and unknown accounts (e.g., reused passwords), can create hidden risks.
Shadow IT—the adoption of tools outside IT oversight—has reached an all-time high. Gartner predicts that by 2025, over 80% of organizations will lack visibility into 40% of their SaaS usage. As these apps become increasingly interconnected, app-to-app connections create another hidden risk of unintentional data exposure.
As decentralized IT becomes the norm, identity security professionals must modernize their strategies to surface hidden risks, prevent identity-related attacks, and adapt continuously to a highly dynamic attack surface.
Savvy: The proactive identity security solution
Savvy takes identity hygiene to the next level by uncovering and addressing blind spots before they’re exploited. Here’s how:
Visibility for all apps and identities
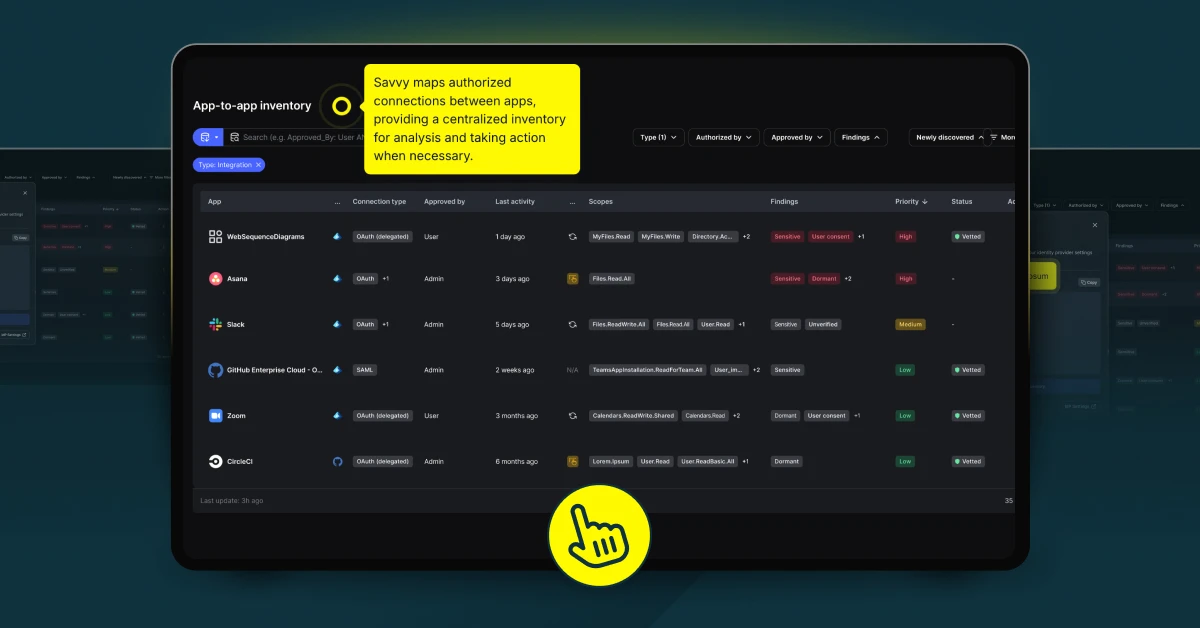
Savvy’s patented technology provides unparalleled insight into SaaS and other app environments, exposing managed and unmanaged shadow IT, unapproved apps, and hidden risks. With continuous app and identity discovery and monitoring, apps are inventoried and a more complete relationship between identities and accounts is maintained.
Surfaces toxic risk
Savvy surfaces toxic risk combinations—like weak credentials paired with missing MFA or unmonitored admin accounts. By proactively surfacing these vulnerabilities, Savvy prevents attackers from gaining traction.
Spotlight MFA and SSO issues
Savvy highlights gaps in MFA enforcement and detects users bypassing SSO. With complete visibility, organizations can enforce consistent security policies across their environments.
Automated Remediation
Savvy doesn’t just detect risks—it resolves them. Automated workflows remediate issues like credential hygiene, misconfigurations, and offboarding gaps in real time, reducing manual workloads for security teams.
2025: The Year to See What You’re Missing in Identity Security
The stakes in identity security have never been higher. With Savvy, you can uncover and mitigate hard-to-detect identity blind spots, protecting your digital environment from identity-based attacks. Don’t let blind spots leave you one password away from a breach. With Savvy, you can see — and secure — hidden risks more effectively and efficiently in 2025 and beyond.