SaaS apps have revolutionized the way businesses operate, providing unparalleled convenience and efficiency. However, with this convenience comes increased susceptibility to credential-related attacks. Weak credentials, misconfigurations, and underutilization of security measures like multi-factor authentication (MFA) have become the leading causes of cloud environment breaches. These issues are now among the most frequent vectors for successful cyberattacks, leaving businesses to grapple with significant consequences.
Credential-related problems are more than minor inconveniences; they can lead to catastrophic breaches that compromise not only your data but also your reputation. For example, the Snowflake breach was directly linked to reused credentials, highlighting the real-world consequences of poor identity management. According to Cybersecurity Dive, nearly half of all cloud attacks in recent years have been traced back to weak or compromised credentials, making it clear that credential security should be a top priority.
Weak Credentials: A Persistent Vulnerability
Weak or nonexistent credentials continue to pose a critical vulnerability for businesses. Despite advancements in cloud security technologies, weak passwords and improper credential management remain the easiest and most common point of entry for cybercriminals. Once they gain access to a weak account, attackers can use legitimate login credentials to move laterally across systems, making it difficult to detect and stop them.
Fact: Weak credentials are the most successful attack vector in cloud environments, making them an easy and attractive target for attackers. The combination of poor password practices, like using default passwords, and inadequate enforcement of security policies leaves organizations wide open for attacks.
Credential Reuse: A Widespread and Dangerous Practice
Credential reuse remains one of the most overlooked yet dangerous cybersecurity risks. In many cases, legitimate credentials are recycled across multiple platforms, creating significant vulnerabilities. When an attacker compromises one account, they often gain access to several others, amplifying the damage they can do.
Despite widespread awareness of the dangers, many users continue to recycle passwords across different platforms, prioritizing convenience over security. This highlights a critical gap in user education on the importance of using strong, unique passwords for every account. Compounding this issue, many organizations lack the tools or processes to monitor and enforce credential hygiene across all applications, leaving them vulnerable to attackers who can easily exploit these weak security practices at scale.
The financial and reputational impacts of such breaches can be devastating. Businesses may face costly remediation efforts, legal penalties, and a significant loss of trust from customers and partners. For regulated industries, weak credential breaches also come with the added risk of non-compliance fines, further increasing the financial burden.
Underutilizing MFA: A Missed Opportunity
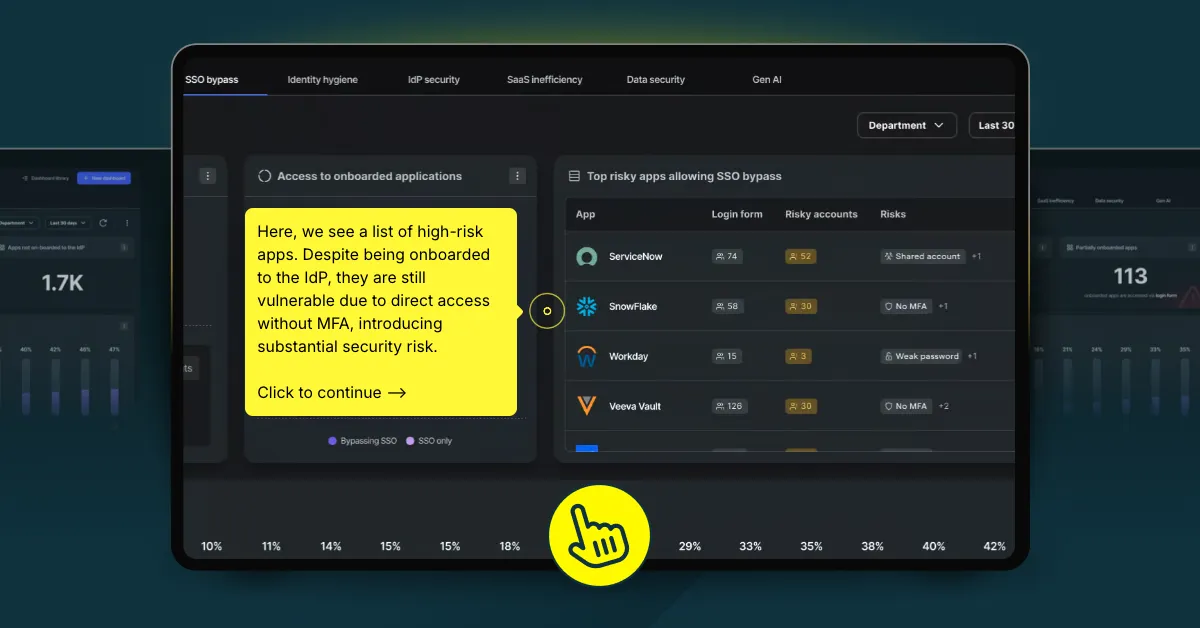
Multi-factor authentication (MFA) is a fundamental security measure that adds an extra layer of protection by requiring users to verify their identity in more than one way. Yet, despite its importance, MFA remains underutilized by many organizations, leaving critical accounts exposed to potential breaches. A major contributing factor is the lack of visibility many organizations have into which apps actually have MFA properly configured. Without this visibility, businesses are left with significant security blind spots, mistakenly believing that their apps are secure when, in fact, many are not.
Complicating matters, some older systems and apps don’t support MFA, making it difficult to implement this essential security measure across the entire organization. Additionally, many employees find MFA cumbersome and intrusive, resisting its adoption. This resistance exacerbates the problem, as organizations may falsely assume that all apps are protected by MFA when they are not.
This lack of understanding extends to both organizations and users, as they often underestimate the crucial role MFA plays in preventing unauthorized access. Without it, accounts—especially those protected by weak or reused credentials—remain highly vulnerable, significantly increasing the risk of breaches.
Misconfigurations: A Growing Risk in Cloud Environments
As cloud infrastructures become increasingly complex, the risk of misconfigurations rises significantly. A growing number of recent breach reports highlight that a substantial portion of cloud-related attacks are directly linked to misconfigured systems, underscoring the importance of proper configuration management. Misconfigurations have become a major vulnerability for organizations, as they can create exploitable gaps in security. Read more about cloud-related breach reports here.
The rapid pace at which cloud systems are deployed often contributes to this problem. In the rush to go live, security configurations are sometimes overlooked or inadequately implemented, leaving systems open to attack. Without thorough and continuous security checks, these configuration errors can linger, providing attackers with easy entry points.
For example, simple errors like incorrectly set access controls or exposed cloud storage buckets can result in widescale breaches. In such cases, sensitive customer information can be exposed, leading to costly regulatory fines and severe reputational damage. Properly managing these configurations is essential to minimizing risk and safeguarding data.
Proactively Identifying Problems with Savvy
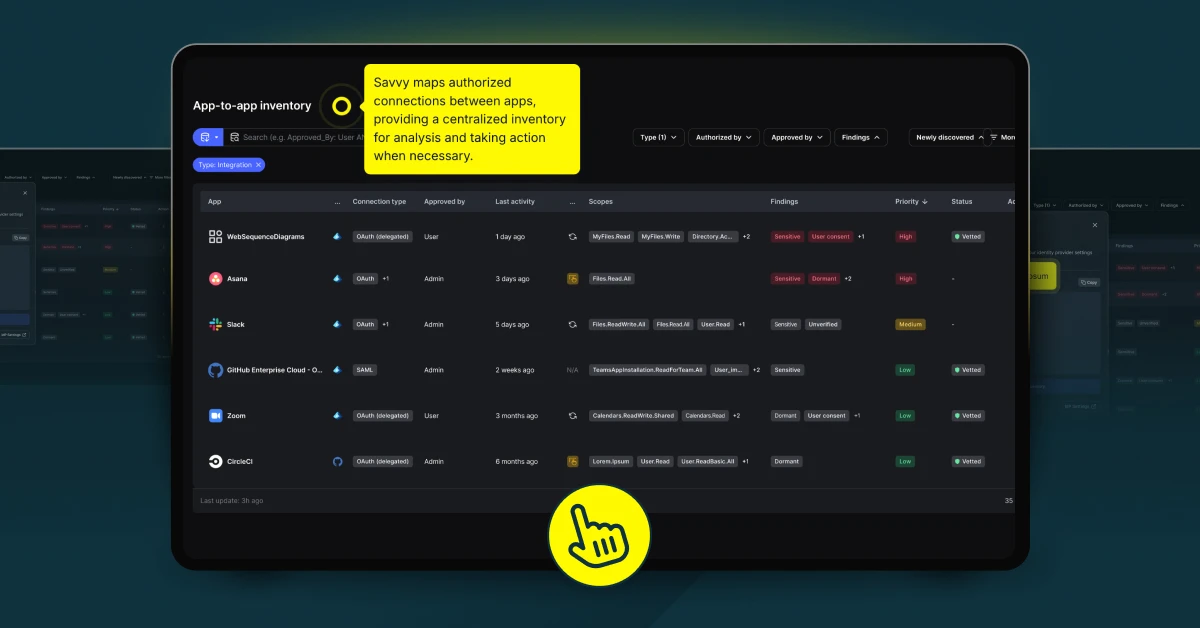
Savvy addresses the top credential and identity risks by taking a proactive approach to SaaS security. With its comprehensive feature set, Savvy helps organizations not only identify vulnerabilities but also take action to mitigate them before they become larger problems.
Enhanced Credential Security: Savvy detects and provides complete visibility into weak, reused, or compromised credentials within SaaS apps, seamlessly prompting users to update their passwords and ensure all credentials meet high-security standards, mitigating the risks posed by weak credentials.
Identify Apps Without MFA Configuration: Savvy monitors and discovers SaaS apps without MFA and provides automated workflows to require users to adhere to the org policies and requirements. Savvy also goes beyond a single point-in-time review to provide continuous validation that MFA is enabled and that users are not circumventing the secondary authentication method, significantly reducing the risk of unauthorized access through stolen credentials.
Credential Integrity Monitoring: Savvy continuously monitors for reused or compromised credentials, alerting administrators to potential risks in real-time. By tracking credential use and ensuring proper identity governance, Savvy helps reduce the risks of credential-based attacks.
Proactive Problem Identification: With real-time monitoring and advanced analytics, Savvy can identify vulnerabilities before they can be exploited, ensuring organizations maintain a secure and resilient environment. Whether it’s weak credentials, misconfigurations, or underutilized MFA, Savvy provides the tools needed to address these issues proactively.
Take Control of Your Identity Security with Savvy
The risks posed by weak credentials, misconfigurations, and underutilized MFA are too significant to ignore. Savvy offers a comprehensive solution designed to tackle these challenges head-on, helping organizations maintain secure SaaS environments and avoid devastating breaches.
Ready to take control of your SaaS security? Schedule a demo with Savvy today and see how we can protect your organization from credential-based threats and misconfigurations.