Organizations are concerned about SaaS proliferation and the numerous untracked and unmanaged applications under their IT umbrella. However, this is not the whole security picture, as they already manage, on average, between 300 and 400 sanctioned applications. These applications are generally approved and integrated into the company’s technological framework with the belief that they are fully secured by existing security protocols. They don’t see the underlying problems based on the sensitive data stored in these applications and the complexities of their configurations and integrations.
This article explores the challenges organizations face securing and managing the identities in their existing apps and provides actionable advice to secure them.
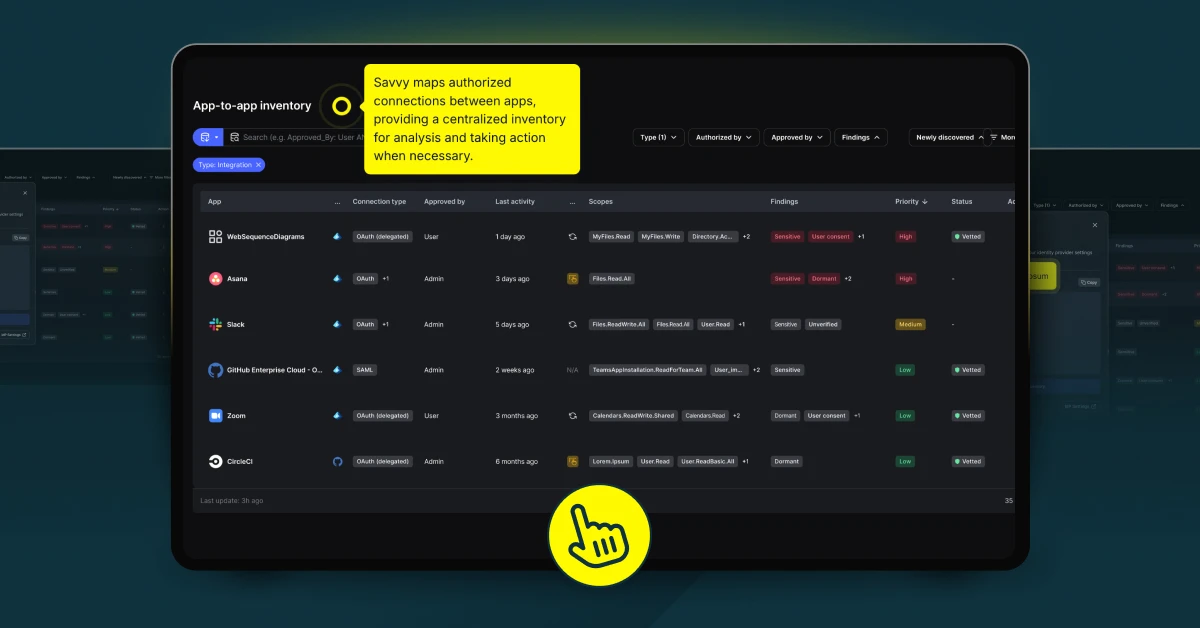
Blindness Assumptions in SaaS Application Monitoring
With the vast quantity of identities accessing an organization’s systems and data, it is challenging to fully perceive and manage them. While the term for this is “identity blindness,” it is more of a gap in visibility. Unfortunately, this leads to a false sense of security for organizations as they are unaware of the problem they cannot fully see, even in applications integrated into an organization’s identity management systems. Many companies operate under the assumption that once an application is officially approved and brought under the umbrella of IT governance, it is inherently secure. This assumption dangerously oversimplifies the complexities involved in true identity and access management.
When organizations fail to recognize that identity blindness can persist even within their approved and integrated systems, they overlook crucial gaps in their security framework. For instance, merely sanctioning an application does not automatically guarantee that proper security measures, like effective access controls or multi-factor authentication, are in place and functioning correctly. This oversight can expose sensitive data and make it vulnerable to unauthorized access from within and outside the organization. The assumption of inherent security often leads to inadequate monitoring of how these applications are accessed and used, increasing the risk of security breaches that can remain undetected for extended periods.
The Risks of Overlooking Sanctioned Apps
Despite being officially approved and integrated into organizational systems, sanctioned apps can still harbor significant vulnerabilities. This false sense of security often leads to complacency, where critical security measures are overlooked or under-implemented.
One of the most glaring oversights in managing sanctioned apps is inadequacies in offboarding processes. Proper offboarding of employees involves revoking their access to all systems and applications. However, this process is not thorough in many organizations, leaving ex-employees with potential backdoor access to sensitive applications and data.
The risks go beyond eliminating ex-employees and extend to how staff access apps. Many sanctioned apps lack robust authentication processes such as Multi-Factor Authentication (MFA). MFA adds an additional layer of protection by requiring multiple forms of verification from users before granting access to systems, making it harder for attackers to use lost or stolen credentials. Failing to discover these control gaps leaves organizations excessively exposed.
Offboarding Challenges and Persistent Access Issues
Effectively offboarding employees is crucial to maintaining organizational security, yet it is fraught with complexities, especially concerning access to sensitive applications. It is a tedious process involving systematically reviewing and revoking all access rights an employee may have accumulated over their tenure. This task becomes more challenging as the number of applications and the granularity of access controls increase, making it more likely for accounts to be overlooked.
Lapses in the offboarding process can result in ex-employees retaining unauthorized access to critical data and systems, providing a potential backdoor through which former staff can access sensitive information, intentionally or unintentionally. These scenarios become more risky for ex-employees who did not leave on good terms or are moving to competitors. The continued access presents opportunities for data theft, sabotage, or data breaches. Even though it ties back to the ex-employee account, proving it was them and not someone who stole or hacked the password is complex, and even if accomplished, the damage is already done.
Prioritizing Comprehensive Security Measures
The only way to combat this problem is to create a holistic cyber defense, extending security measures to encompass sanctioned and unsanctioned software throughout the IT ecosystem. This involves building a process of regular security audits, real-time monitoring, and integrating advanced technologies such as artificial intelligence and machine learning for detection.
Best Practices for Managing Sanctioned App Security
Building this comprehensive practice can start with some basic steps and best practices to create a secure foundation. Enforcing strict authentication controls is one of the first practices. Implementing robust authentication measures such as MFA is crucial. MFA should be mandated to add an additional layer of security, requiring users to provide two or more verification factors before accessing sensitive systems and data. Similarly, enforcing password complexity guidelines is essential to strengthen user credentials, which includes setting requirements for password length, complexity, and expiration, which help mitigate the risk of breaches due to weak or reused passwords.
Regular security audits of accounts for apps build on this foundation. It helps ensure that only authorized personnel access sensitive apps and data, minimizing the risk of insider threats and reducing the potential damage from compromised user credentials. This process is critical for compliance with various regulatory standards, such as GDPR, HIPAA, or SOX, which require stringent access controls and record-keeping.
Audits help verify that the organization’s access controls are functioning as intended and highlight any discrepancies that might expose the organization to risks of data breaches or non-compliance penalties.
Continuously monitoring SaaS app usage provides long-term oversight. It involves tracking who accesses the applications, when, and their actions. Continuous monitoring helps quickly detect unauthorized or suspicious activities, enabling timely interventions to prevent potential security incidents and providing valuable insights into user behavior patterns, which can further refine security policies and controls.
Sprawl Stop SaaS Sprawl with Savvy
Savvy assists organizations in effectively managing their SaaS environments through a sophisticated, identity-first strategy. This approach lets organizations thoroughly explore and comprehend their SaaS landscape and operations. With Savvy, businesses can assess risky access combinations, reveal concealed IT resources driven by business needs, and simplify compliance procedures.
Take control over SaaS security, making it part of your overall IT organization rather than an exception. Schedule a demo to see Savvy in action.