
Awareness
Discover up to 4 times more SaaS apps including rogue Generative AI (Gen AI) usage
Analytics

Ensure critical apps are onboarded and reduce SSO bypass by 86%
Action
Learn more about the Savvy Platform
The Savvy
Difference
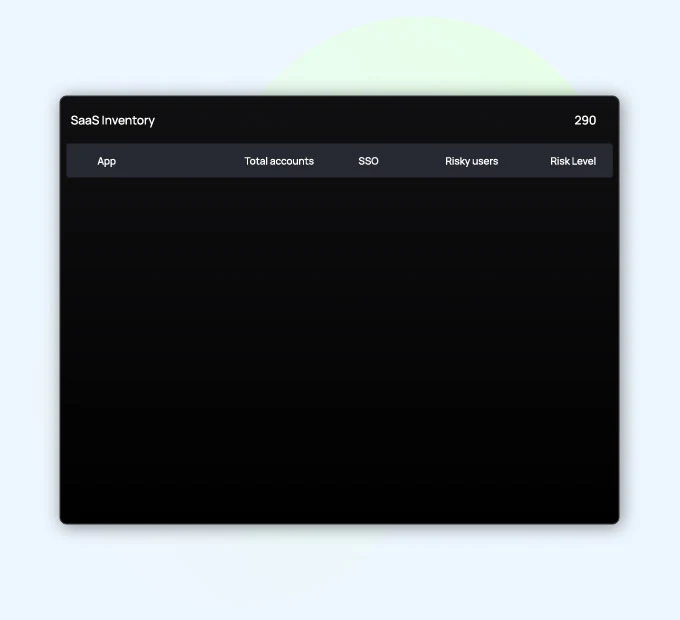
Real-Time
Inventory
Savvy delivers a real-time inventory of every SaaS app and identity, giving you full visibility into accounts and authentication methods across your ecosystem. Use it to prioritize business-critical apps for SSO onboarding, or to uncover toxic combinations of risks, like accounts lacking MFA that are using compromised credentials. With this enhanced visibility, you can implement adaptive controls that ensure stronger alignment with your IT and security policies.
Just-In-Time
Security Guardrails
When a security risk is detected, Savvy deploys real-time interactive guidance, powered by pre-built or custom playbooks, to help users quickly and safely navigate issues on their own–saving you and your team time. For example, Savvy can prompt users to enable private mode in ChatGPT or prevent the use of risky credentials in unmanaged apps. This ensures users remain productive while following security best practices.
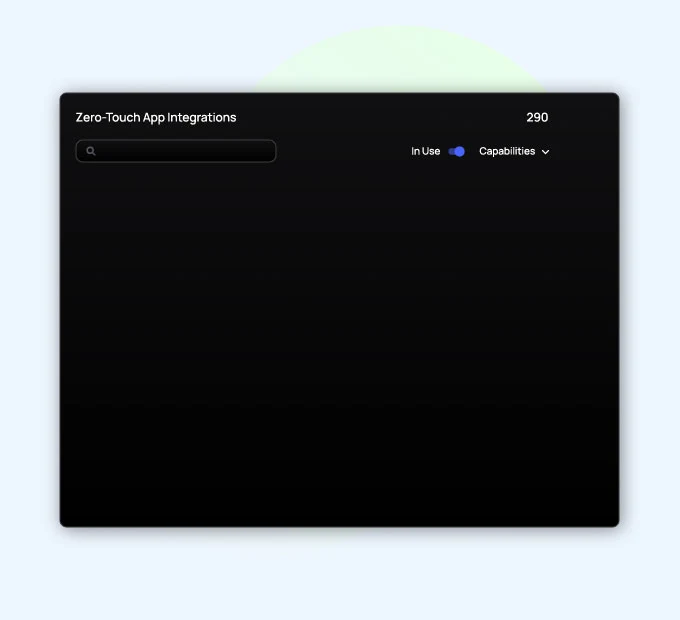
Zero-Touch
Integrations
Zero-Touch Integrations (ZTI) revolutionizes SaaS governance with its patent-pending client-side technology, seamlessly integrating and managing SaaS apps without manual server-side configuration. ZTIs boost the effectiveness of your existing IAM and IGA tools, empowering you to discover and eliminate dormant or unmanaged accounts, identify privileged users, and easily offboard users from sanctioned and unsanctioned apps with ease.
Savvy
Use Cases

Shadow IT & SaaS Sprawl
Continuously discover apps and regain control over SaaS. Govern, consolidate, and eliminate unnecessary apps to improve security and lower SaaS spend.
User Offboarding
Efficiently revoke access and deprovision access across your app ecosystem for movers and leavers.
Identity Hygiene
Detect and guide users to clean up risky credentials and enable SSO and MFA for enhanced security. Orchestrate guided workflows or execute cloud-based actions via APIs.
Trusted by
Get a 30-Minute
Complimentary Assessment
Recent Updates









