Attackers frequently steal passwords through phishing scams or exploit them using credential stuffing attacks, where they reuse stolen credentials from one site to gain access to other sites. These attacks are extremely common, with Okta reporting that they account for almost 80% of login attempts on retail, financial services, and entertainment sites. Even with a low per-guess success rate of 0.1%, the ease of attack and volume means it only takes 1000 stolen accounts before something yields access.
Multi-factor authentication (MFA) helps prevent these attacks by requiring one more step for attackers, making it harder to blast out login attempts. Even if there is a match, the attack falls flat without the extra factor from MFA.
What is MFA?
MFA is a robust security system designed to enhance the protection of user identities by requiring multiple authentication methods from different categories of credentials. Instead of relying solely on a password, which can be easily compromised, MFA requires additional layers of verification. Users are required to provide something they know (such as a password or PIN), something they have (like a code sent to their phone or a security token), and/or something they are (such as a fingerprint scan or facial recognition). This multi-layered approach significantly increases security, making it much more difficult for unauthorized users to access sensitive information and systems.
MFA Work in SaaS Application Monitoring
MFA uses different types of security factors to verify a user’s identity. These factors are categorized into three main types:
- Knowledge Factors: This involves something the user knows, such as passwords or PINs. It is the traditional form of authentication in which the user must recall specific information.
- Possession Factors: This includes something the user has, such as a mobile phone, security tokens, or a smart card. These items generate or receive unique codes that the user must enter to complete the authentication process.
- Inherence Factors: This pertains to something the user is, which involves biometric data like fingerprints, facial recognition, or voice recognition. These factors are unique to the individual and are often considered the most secure.
The typical process flow of MFA is as follows:
- The user starts by entering their password.
- They are then prompted to provide a second form of identification, such as a code sent to their mobile phone or a fingerprint scan.
- After successfully verifying the additional factor, the user gains access to the system or application.
MFA significantly enhances security by adding extra layers of protection. Even if a password is compromised, the additional verification steps make it much more difficult for unauthorized users to gain access. This layered security approach reduces the risk of breaches and helps protect sensitive data from cyber threats.
Challenges in Using MFA in SaaS App Monitoring
While MFA significantly enhances security, it presents several challenges that organizations must address. One of the main issues is usability. Users may need help to use multiple authentication methods each time they log in, leading to frustration and decreased productivity. Additionally, there are accessibility concerns, as specific authentication methods might be complicated for users with disabilities, posing barriers to inclusivity.
Another significant challenge is the implementation cost. The initial setup of MFA can be expensive, requiring substantial investment in both hardware and software. Furthermore, ongoing maintenance involves continuous updates and support, which can add to the overall expense. This financial burden can be a deterrent for some organizations.
User resistance is another hurdle. Users accustomed to single-factor authentication may resist transitioning to MFA due to the additional steps required. This resistance can stem from a perceived inconvenience, as users might view the extra authentication steps as time-consuming and unnecessary.
From a technical standpoint, integrating MFA with existing systems can be complex and challenging, often requiring significant effort and expertise. Ensuring compatibility across various devices and platforms can also be difficult, leading to inconsistent user experiences.
Backup and recovery pose additional challenges. Managing lost or stolen devices used for authentication can be problematic, necessitating robust procedures for backup and recovery. Providing alternative authentication methods for users who cannot access their primary method is essential but can further complicate the system.
Despite these challenges, MFA’s security benefits make it a crucial component of a comprehensive cybersecurity strategy. Organizations must carefully consider these factors and work towards solutions that balance security with user convenience and accessibility.
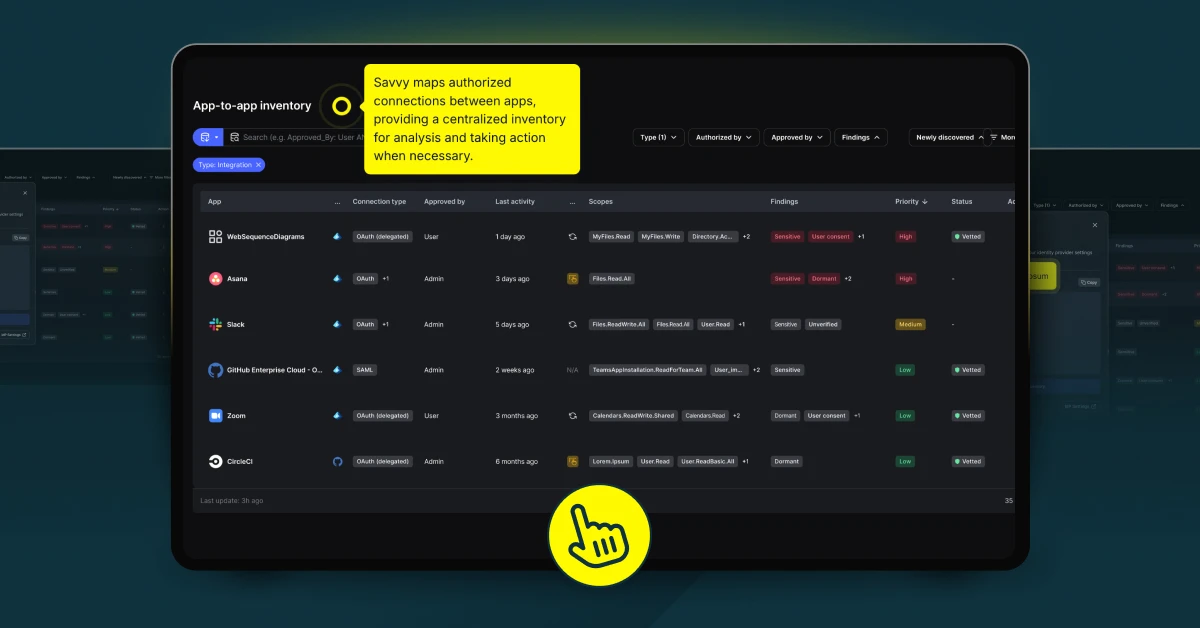
Consistent MFA using Savvy for SaaS App Monitoring
Savvy Security is dedicated to enhancing the security of your SaaS environments by identifying and addressing poorly configured systems, including those lacking MFA. Organizations rely on various SaaS apps, but improper configurations can leave these systems vulnerable to cyber threats.
Savvy Security provides advanced solutions that automatically scan and analyze your SaaS apps to detect configurations that do not meet security best practices. This includes identifying instances where MFA is not enabled or properly configured, a critical defense layer against unauthorized access.
Through its robust and scalable technology, Savvy Security ensures that your SaaS apps are secure and compliant with industry standards. The platform seamlessly integrates with your existing systems, providing comprehensive visibility across all your applications. This integration supports a wide range of devices and applications, ensuring that no aspect of your SaaS environment is overlooked.
Take control over SaaS security, making it part of your overall IT organization rather than an exception. Schedule a demo to see Savvy in action.
FAQ
- Question 1: What impact does MFA have on user experience?
- Answer: Although MFA adds an extra step to the login process, it can be designed to minimize disruption and maintain a positive user experience.
- Question 2: What are some common MFA methods?
- Answer: Common methods include SMS codes, authentication apps, security tokens, and biometrics.
- Question 3: Are there any industries where MFA is especially critical?
- Answer: MFA is particularly important in industries that handle sensitive information, such as healthcare, finance, and government.