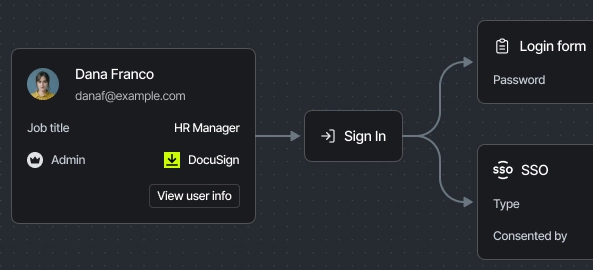
Capture Authentication MethodsMany apps retain local accounts after onboarding to your Single Sign-On (SSO) solution. Identify SSO bypass activity using observed activity in the browser. Also validate that Multi-Factor Authentication (MFA) is enabled and working as intended to improve resilience to identity-based attacks. |
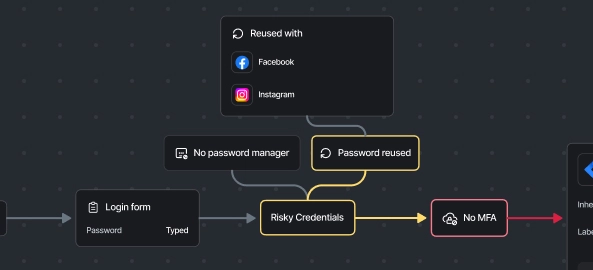
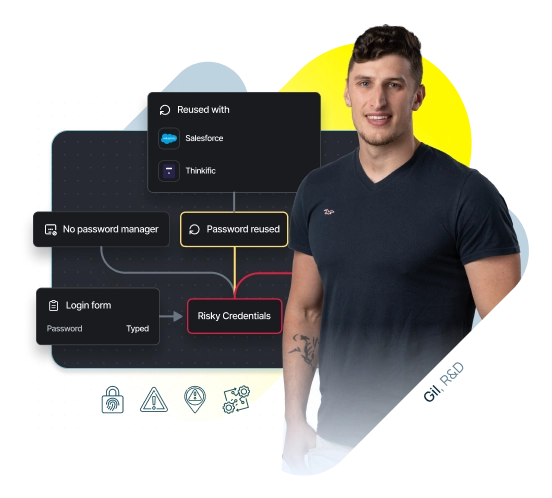
Detect Risky CredentialsRisky credentials that use weak, reused, shared, or compromised passwords can co-exist alongside your centralized accounts, leaving a critical backdoor open for threat actors. |
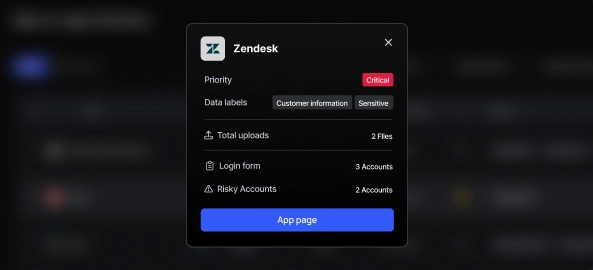
Map App Access and Risk LevelsUnderstanding which apps an identity has access to is fundamental to assessing the risk it introduces. Moreover, the apps themselves have inherent risk levels based on the app types and the types of data observed to transfer in and out. |
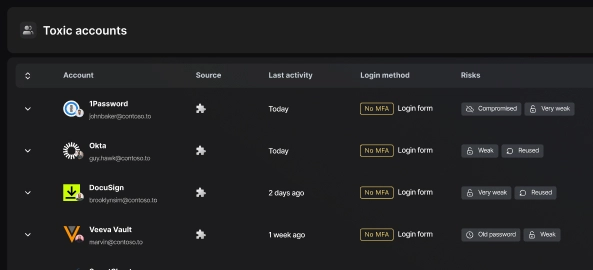
Surface Toxic Combinations of RiskArmed with a full picture of the identity, Savvy evaluates risks that, when combined, represent a toxic risk to the organization. |
Speed Situational
Awareness
Visualize how identity attributes are interrelated to quickly understand the risk factors that lead to toxic accounts.
Strengthen Security
Posture
Catch identity security issues that other offerings miss and automate the remediation to improve security posture at scale.
Drive Operational
Efficiency
Reduce time spent sifting through spreadsheets of data to find the most critical identity-related risks.
Explore Toxic Risk Combinations
in Real-Time Demo
Learn more about the Savvy Platform
Get a 30-Minute
Complimentary Assessment
Related Resources