Resources
The latest insights from the Savvy team & Cybersecurity Space

As we see evidence of time and again, threat actors don’t always hack—sometimes they simply log in. The PowerSchool breach is the latest example of how credential-based attacks are surging, putting organizations of every type at greater risk. A single weak password, an unmonitored app, or a misconfigured access policy can become the entry point […]

Blog
January 21st, 2025
As we see evidence of time and again, threat actors don’t always hack—sometimes they simply log in. The PowerSchool breach is the latest example of how credential-based attacks are surging, putting organizations of every type at greater risk. A single weak password, an unmonitored app, or a misconfigured access policy can become the entry point […]

Blog
January 6th, 2025
Imagine this: your security team spends hours investigating a flagged credential breach, only to find out the password has been changed, or the account has robust MFA in place, making it non-exploitable. Meanwhile, real threats linger unnoticed, buried in a sea of false positives. The reality is that relying solely on traditional threat intelligence tools […]

Blog
December 23rd, 2024
Identity takes center stage In 2024, identity solidified itself as the de facto security perimeter for modern enterprises. Yet blind spots—like SSO Bypass, misconfigured MFA, and credential hygiene—remain major issues that most organizations miss entirely. To stay ahead of breaches, we predict organizations will begin to tackle these gaps in 2025 in order to fortify […]

Blog
December 16th, 2024
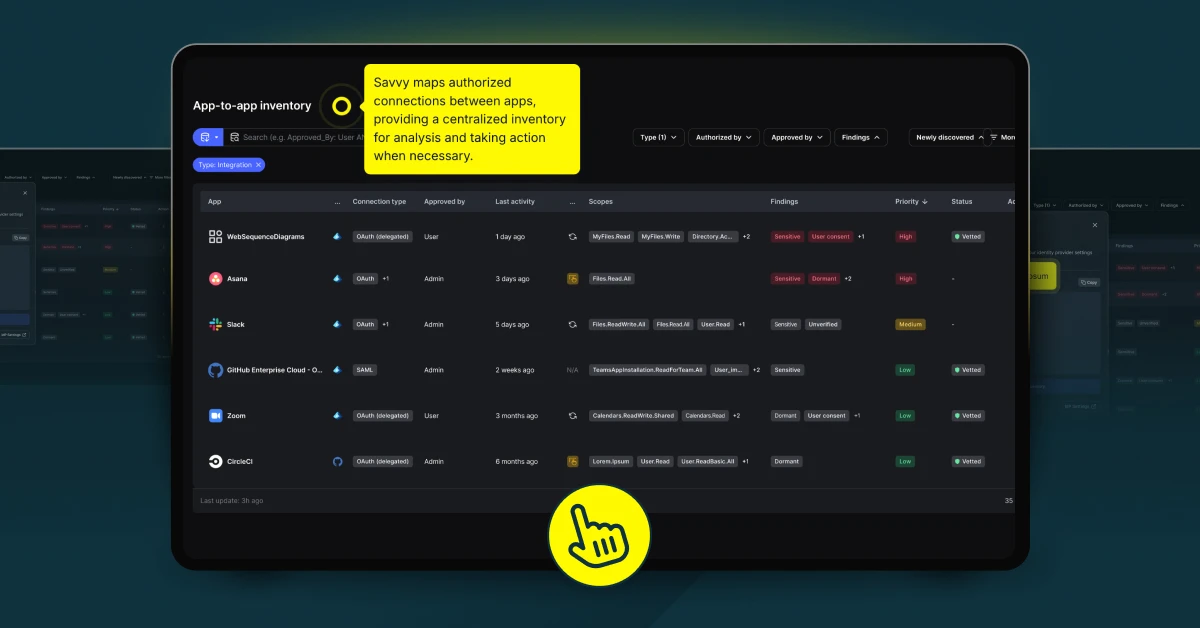
The Hidden Risks Lurking in App-to-App Connections As SaaS ecosystems grow, app-to-app connections have become the backbone of modern productivity, enabling seamless workflows and enhancing efficiency. However, with these benefits come unprecedented security challenges. Many organizations remain unaware of the risks posed by interconnected apps—particularly when unmanaged or poorly configured connections expose sensitive data. Shadow […]

Blog
December 10th, 2024
The technical sophistication of phishing-as-a-service kits has reached a level that poses a direct threat to The technical sophistication of phishing-as-a-service kits has reached a level that directly threatens organizations that are still relying on weak multi-factor authentication (MFA) methods. Now, cybercriminals have never had it easier. For a mere $200, they can purchase a […]
Demos
December 9th, 2024
App-to-app connections enhance productivity, but they also create hidden vulnerabilities that attackers are quick to exploit. In this demo, uncover how Savvy identifies and mitigates these risks by mapping every human and non-human identity, analyzing permissions to eliminate excessive access, and continuously monitoring interactions in real-time. See how Savvy dynamically discovers app connections, maps them […]


Blog
December 2nd, 2024
Compliance frameworks like the NIST Cybersecurity Framework (CSF) have become essential blueprints for building resilient security programs. While organizations race to meet NIST standards, the rapid adoption of SaaS apps has introduced significant challenges in maintaining compliance, visibility, and control over identity and access. Enter Savvy, an identity-first solution designed to bridge these compliance gaps […]
